Email blacklists (aka email blocklists) publicly name the internet’s most notorious spammers. Domains that land on one can find themselves locked out of inboxes and ISPs. What can you do to avoid this fate? We have the answers for you right here.
Email blacklists are your friends.
It may not seem that way initially, but they keep subscribers’ inboxes clean from spammers, allowing legit email marketers like yourself to shine.
One can even think of them as the sheriffs of our age.
That’s because the internet is a bit like the old American Wild West. It’s full of opportunity — but that opportunity draws rogues and ruffians as well as honest folk.
Spammers and scammers are the outlaws and bandits of the digital age. If they had their way, the internet would be a thoroughly lawless place.
Fortunately, the internet also has plenty of people working to build a lawful, peaceful online society where people can live free from the fear of fraudsters.
ISPs, government regulators, email clients, and all kinds of other groups may not always agree about how the internet should run — heck, they may even compete against each other — but they’re willing to put their differences aside when it comes to fighting spammers.
One of the tools they use to keep spammers at bay is email blacklists. These modern-day most wanted posters tell ISPs and email clients which IPs to be on the lookout for to keep their email users safe.
And let me tell you: You don’t want your domain’s IPs to land on one of these lists, pardner.
Keep reading to discover exactly what email blacklists are and how you stay off of ‘em.
The first email was sent in 1971, and shortly thereafter, the settlement of the internet began.
Early internet adventurers found a place to set up their inboxes and began doing business in the digital version of the American Wild West. By 1978, the first spam appeared in some of those inboxes. (Okay, maybe it isn’t fair to call that first mass unsolicited mailing “spam.” I’m sure it seemed like an innovative marketing idea at the time.)
Since those early days, some parts of the internet have been tamed. But despite efforts by government regulators and independent operators to shut down spammers, these inbox trespassers remain a problem.
How ornery are these outlaws?
Real ornery.
Folks living in the United States reported email scams totaling $252 million in losses to the Federal Trade Commission (FTC) in 2020. Phishing emails cost the U.S. another $54 million.
IC3’s 2020 annual report reveals more than $1.8 billion in losses from Business Email Compromise and Email Account Compromise scams involving unauthorized fund transfers. Internet criminals used email phishing scams to execute ransomware campaigns.
And when they’re not stealing and ransoming, email spammers are just being a plain nuisance. Nearly 85% of all the emails sent every day are spam.
Not all that spam ends up in email users’ inboxes, though. Email service providers (ESPs) work hard to keep their customers’ inboxes clear of unwanted emails using several strategies, including blacklists.
What is an email blacklist?

An email blacklist is a digital rogues’ gallery. It’s a database that records the IP address and/or domain name of outlaws who’ve been caught sending spam, as well as their known associates or the servers guilty of harboring them.
Email blacklists are sometimes called by their fancy names, Real-time Blackhole Lists (RBLs), or Domain Name System blacklists (DNSBL), depending on whether they list domain names or IPs.
Most of today’s blacklists include both types of identifiers. These traditional blacklists identify bad actors by their sending IP addresses. But with additional technology, spam fighters can dig even deeper, examining not only the sender’s IP but also the content within the emails being sent.
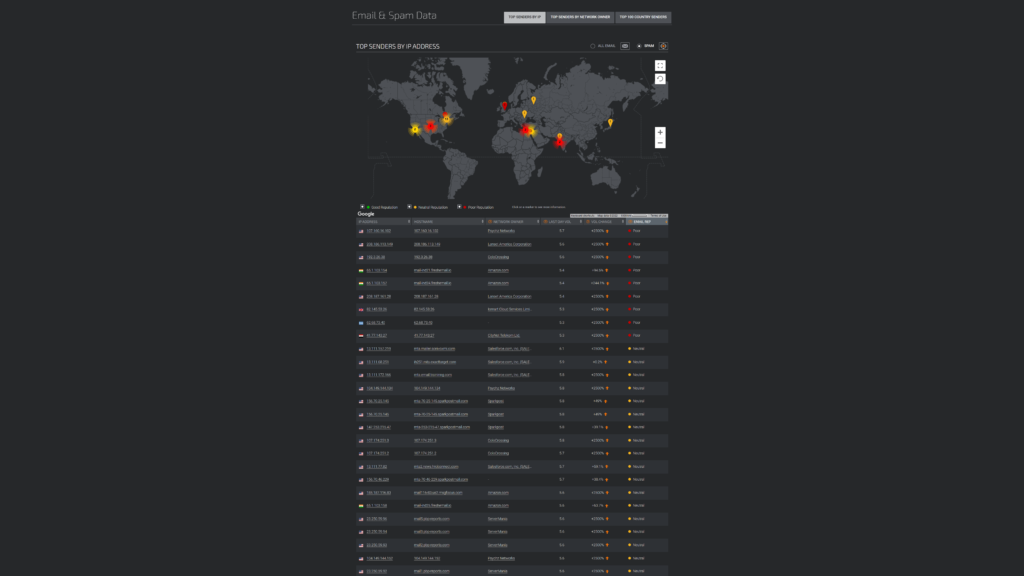
Talos Intelligence publishes a variety of IP lists rating send rates and reputations, including a list of top spammers.
Content blacklists check the content of incoming emails for links to domains that have been identified as malicious. This prevents outlaws from sneaking into town via legitimate IP addresses. Features such as Microsoft’s Safe Links use content blacklists to keep its users’ inboxes secure.
Many corporations and every email client maintain private blacklists where they identify the sending IP addresses or domain IPs that aren’t welcome in their towns. These internal blacklists can mean your email messages arrive in some inboxes just fine and never reach others.
There are public blacklists too. These lists include known troublemakers, and the list owners keep them updated with whatever ne’er-do-wells they catch. Like bounty hunters, blacklist owners are always on the lookout for outlaws they can help bring down.

Spamhaus is one of the most influential public blacklists.
Email blacklists help maintain order across digital territories by identifying bad actors. But, now and then, these lists also include the IPs of senders only suspected of being spammers.
Folks like you may have accidentally stepped over a line or been hanging out on the wrong servers. When that happens, you’ll need to deal with the consequences while you try to get yourself delisted.
What happens if you end up on a blacklist?
Public blacklists work closely with ISPs, with many offering free access for manual checks and subscription services that enable organizations to conduct real-time bulk checks of the emails passing through their servers.
ISPs and other email service providers may use the data obtained from these blacklists as the sole factor when deciding how to process a message or as part of a scoring system that decides an email’s fate.
If your IP shows up on a blacklist, the ISP may:
- Decide you aren’t welcome in their town (or their users’ inboxes) and give you a hard bounce.
- Let you into town but take you straight to jail (a.k.a. the spam folder).
- Let you pass on through to subscribers whose previous engagement with your messages indicates that they don’t mind a visit.
Even if landing on a blacklist doesn’t necessarily mean you won’t make it to your subscribers’ inboxes, you should still try to avoid being on these lists. Being on a blacklist can do more than hurt your email deliverability.
Getting listed is bad for your domain reputation. If your sending domain gets caught on the wrong side of the law too many times, the internet community will suspend and shun you.
ISPs don’t want to have their servers sullied by your bad behavior. SMTP relays may not let you pass through their territory, and that local hideout you were using to send your messages may kick you out.
Just how bad things get depends on how influential the particular email blacklist is. Some blacklists have more credibility than others. (I’ll share my “top blacklists to watch” list later.)
Before we look at the top blacklists, though, here’s a list of reasons you may end up on one.
How can you avoid being labeled a spammer by an email blacklist?

Blacklist publishers identify the domains and IPs for their lists by gathering direct and indirect information about senders’ activities. Some activities, such as delivering malware to email recipients, are undoubtedly blacklist-worthy. Other activities aren’t so clear — both spammers and legitimate emailers might behave in a given way.
In these situations, whether something is spam may depend on your point of view. If ISPs and email recipients perceive your messages as unwanted, you can end up on a blacklist even if you think you don’t belong there.
Here’s a round-up of what to do and not to do to stay off the digital Wild West’s most wanted lists.
Don’t send emails that contain malicious links, fraudulent offers, or other scams
Well, yeah, this one’s pretty obvious. If your sending IP is associated with illegal activities, you’re going to be labeled as an outlaw.
Besides not engaging in these activities, pay attention to the company you keep. Make sure you don’t include links to blacklisted websites in your email’s content.
SURBL.org’s URI reputation data lists websites that appear in unsolicited emails. These sites aren’t senders, but are suspected participants in spam activity.
Don’t send unsolicited emails to people with whom you have no connection
Maybe you aren’t scamming, but this action will get you listed for spamming. While there are some exceptions for business-to-business or transactional emails, consumer privacy and anti-spam laws, including the EU’s General Data Protection Regulation (GDPR), Canada’s Anti-Spam Law (CASL), and the US CAN-SPAM Act, are pretty clear: Don’t send emails without permission.
Stay in compliance and avoid drawing unwanted attention from blacklists by practicing good list-building behaviors. Send your messages only to individuals who have actively opted in to receiving them. Don’t create sign-up forms that make opting in the default choice.
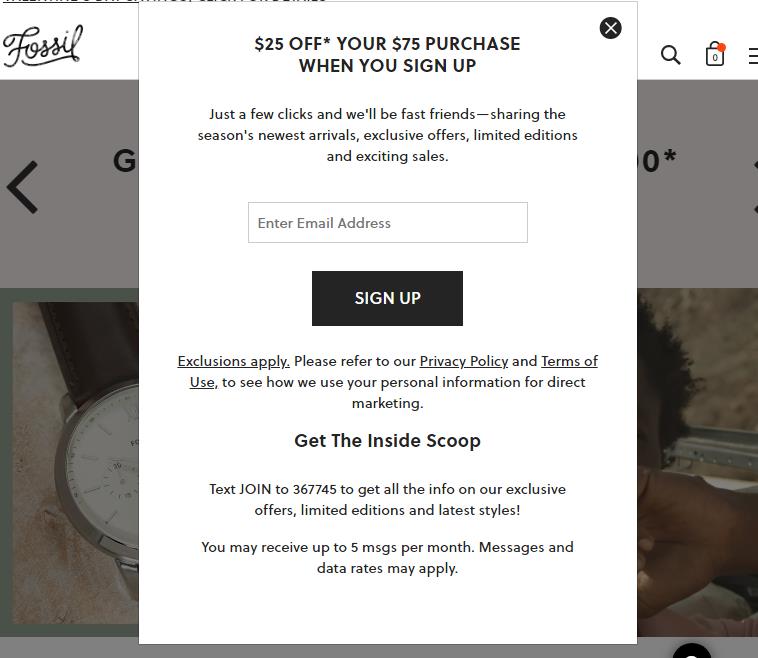
Fossil’s sign-up form explains what subscribers can expect and provides them with links to the brand’s terms and privacy policy.
Your sign-up forms should make clear what the person who opts in is agreeing to receive.
Improper list-building tactics (with purchasing or scraping email addresses at the top of this list) will result in low engagement and high spam complaint rates. That’s a bad combination.
Plus, if your list-building practices aren’t pure, you’ll get caught in spamtraps–guaranteeing your place on a blacklist.
Steer clear of spamtraps
blacklist publishers don’t just sit around waiting for bad guys to show themselves. There’s a bounty to be had for turning in spammers.
Blacklists that maintain the most accurate, up-to-date lists earn reputations for being reliable, translating into increased revenue through subscriptions and other channels.
So blacklists set traps: Spamtraps.
Spamtraps are email addresses that don’t belong to an active end user. These emails exist only to catch senders in the act of emailing non-subscribers.
How do these spamtrap addresses end up on your email lists?
Some traps are recycled emails. These are emails that belonged to a real person once, but that person hasn’t used the address for a long time.
Since an email client knows when an address is active or not, it can use these inactive email accounts to monitor senders’ behavior. If you’re sending messages to a long-dormant account, the email client knows you aren’t paying attention to your subscriber engagement.
The recycling cycle doesn’t stop there, though. blacklists can purchase sets of dormant emails from mailbox providers and use these emails to set their own traps by monitoring incoming messages or redistributing the emails to places where spammers go to collect addresses.
blacklists don’t always plant recycled email addresses to catch spammers. They also create spamtraps with pristine emails that never belonged to a legitimate user.
The blacklist simply generates a set of email addresses, places them on various internet properties, and monitors them. It’s easy to prove that a sender doesn’t have permission to send an email if there’s no one who could have given that permission. Busted!
Finally, typo spamtraps are email addresses that aren’t valid because of some error in the address itself. They may contain a misspelled domain name, for example.
These typo traps may have been created by accident, but the results are real for senders who keep them on their subscription lists. When you send to one of these invalid addresses, the email will bounce back and the mailbox provider may register you as a bad sender.
It’s easy to stay out of spamtraps if you engage in both good list-building and list-hygiene practices.
- Obtain email addresses directly from subscribers and not third-party sources.
- Use real-time or bulk email validation to avoid being tripped up by typos.
- Employ a double-opt-in strategy to make sure entered emails belong to a genuine subscriber who wants to receive your messages.
- Execute re-engagement campaigns to ensure that everyone on your list is still around.
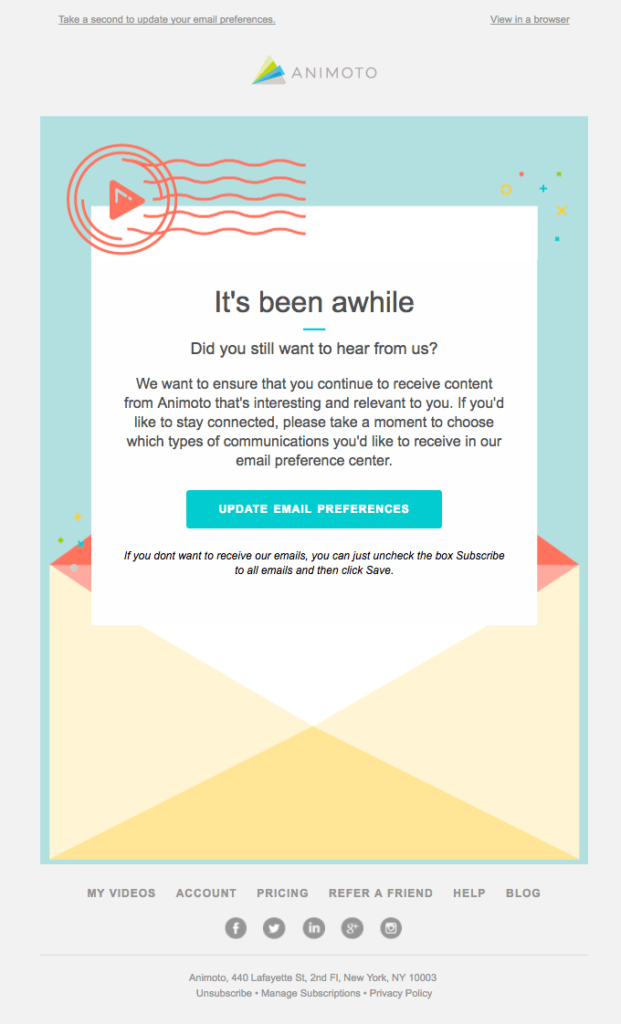
This email from Animoto asks subscribers to check in and confirm their continued interest in hearing from the brand.
- Establish and automate a sunsetting policy that removes dormant emails from your subscription lists.
- Schedule regular list check-ups. Review engagement levels, bounce, unsubscribe and complaint rates, and revalidate your lists to identify potential problems.
Avoid sending like a spammer
It may not seem fair, but when it comes to staying off email blacklists, appearances matter.
Engaging in activities that resemble those of a spammer might not be a one-way ticket to being listed. However, every signal adds to the whole. If your cumulative sending behaviors start to resemble a spammer’s profile, you can end up on an email blacklist.
What makes ISPs suspect you of being a spammer and share those suspicions with blacklists?
Spammers are constantly acquiring new email addresses in an effort to increase email volume and revenue. As a result, spammers’ sending patterns are erratic.
The volume and timing of their emails change frequently, as do their lists of recipients. The content, on the other hand, is often the same as they use the same message to target new victims.
Outlaws on the run in the Wild West could only get so far before they wore out their horses. The wiliest of outlaws kept fresh horses in waiting and would switch rides to keep ahead of bounty hunters and sheriffs’ posses. Spammers do this too, only they switch out IPs.
To prevent your sending behaviors from raising alarms:
- Maintain steady sending volumes and frequencies. Be consistent about the days and times that you send your bulk messages.
- Warm up new IPs by gradually increasing the number of emails you send. Save yourself time and effort by using Ongage’s automated IP warm-up process.
- Be cautious about using shortened links. While shortening a URL may seem like a legitimate way to enhance your subscriber’s experience, scammers sometimes use this strategy to obscure the link’s destination. Your messages may earn a closer look from mailbox providers if your links’ destination is unclear.
- Make sure your email header and sender address match your domain and From name. A mismatch between your sender domain and your reply-to or other message URLs can attract suspicion because spammers sometimes can’t keep everything aligned when moving between domains and IPs.
- Avoid sending the same email message to different email lists over a series of days or weeks, or sending the same message to your recipients more than once. Change your subject line and update your email’s body text when sending a reminder or follow-up message that must repeat previously sent information.
- Don’t send messages that include hidden text or poor-quality images. And be cautious when sending image-only emails. Spammers sometimes place their ill-intended messages in an image format to avoid detection by text-based filters.
Following good sending practices helps you avoid blacklists and improves your deliverability.
Email clients that detect these suspicious behaviors may throttle your access to their users, bounce your messages back to you, or, in a best-case scenario, send them directly to users’ inboxes.
Be proactive about preventing spam complaints
Email recipients play a role in the battle to keep inboxes safe, too. They defend their inbox and alert their mailbox provider to troublesome senders by reporting the emails they receive as spam. Spam complaints by users signal to mail providers that you aren’t a welcomed visitor.
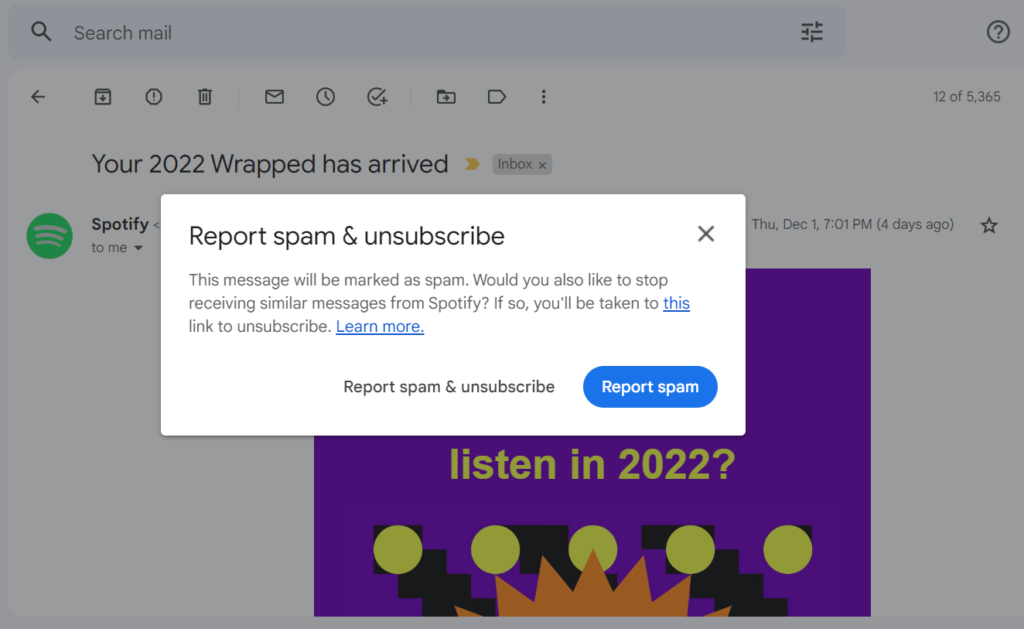
Gmail has a built-in option that lets recipients conveniently mark and report unwanted emails as spam.
Getting a few complaints now and then isn’t a problem. But if you are a common subject of complaints, you can expect to be treated like an outlaw.
Reasons emails get marked as spam
From the consumers’ perspective, any email they don’t want to receive is spam. This is another reason (aside from the legalities) to make sure you have people’s consent before you send them an email.
But let’s assume you have permission and are only sending your messages to people who have signed up for your email list.
Why would those emails get marked as spam?
It could be forgetfulness. Maybe your subscriber forgot they agreed to receive your emails. You can help prevent this by sending new subscribers a welcome message that explains why they are hearing from you. It doesn’t hurt to place a reminder in the footer of every email, either.
Brass Roots includes a short note at the end of its emails telling subscribers why they’re on the list, along with the brand’s contact information and other details.
It could also be miscommunication. Maybe you got an opt-in from your subscriber, but you weren’t clear about what it was they were opting in to receive. Does your sign-up form adequately set the stage for your future communications by telling subscribers what to expect?
Sometimes, subscribers will mark your messages as spam because they can’t find an easier way to stop receiving them. If your unsubscribe options are difficult to locate or if you don’t immediately honor unsubscribe requests, unwilling recipients will resort to the next best option: Marking your messages as spam.
It may seem counterintuitive, but you’ll be doing your sender reputation and your deliverability a favor by making it easy for subscribers to unsubscribe from your list.
Use a list-unsubscribe header and always include an unsubscribe link in your footer.
NordVPN includes an unsubscribe header so recipients have no reason to hit the spam button.
Automate adding unsubscribed addresses to your suppression list so that you don’t continue sending unwanted emails.
Your messages may also be marked as spam if you send too many or if your recipients don’t like your content. Low-effort, low-value content isn’t welcome in most inboxes, particularly when it arrives frequently.
Preempt spam complaints (and low engagement) by paying attention to how your subscribers respond to your emails. Look at click-through rates and ask for feedback about your content and sending cadence to fine-tune your process.
Vogue gets a feel for recent subscribers’ engagement and satisfaction levels in this response-requested email.
Put control of their inboxes into your subscribers’ hands by providing them with preference centers packed with people-pleasing options. Add this link right next to the unsubscribe link in your footer so that subscribers who want less contact can let you know.

Songkick’s footer provides subscribers with all the links they need to stay in control of their communications with the brand.
And, of course, create content that is tailored to your audience. Use segmentation and dynamic content to develop personalized messages that add value and encourage interactions with your brand.
When your subscribers consistently engage with your emails by opening them, clicking through to your content, or forwarding them, this signals to email service providers that you are a good inbox citizen.
Finally, give your subscribers every reason to trust your brand and its emails by:
- Using a recognizable From name and further legitimizing your sending name by adding a Brand Indicator for Message Information (BIMI) logo when possible.
- Making sure your graphics are high-quality and relevant.
- Performing quality assurance tests to ensure that your messages render properly across devices and your links are unbroken.
- Avoiding grammatical errors and misspellings in your copy and limiting your use of over-the-top language or formatting that may be perceived as spammy.
- Providing recipients with contact information and a way to reply to your messages.
These steps contribute to the overall impression your emails make with subscribers. Your goal should be to ensure that impression is positive.
Secure your sender reputation and email chain of custody to prevent hijackings
Imagine a situation where your stagecoach rolls into town all nice and innocent-like. Then, suddenly, a bunch of bandits spill out from the carriage and start robbing and stealing the townsfolk.
After the dust settles, you could try appealing to the local constabulary to convince them you had no idea what your passengers had planned.
But will they believe you?
It’s up to you to protect your sender reputation and your email subscribers so bandits never get a chance to hitch a ride on your wagon.
Your sending name or email content may be used to infiltrate users’ inboxes if you don’t take necessary security precautions, like implementing authentication protocols that allow SMTPs and ISPs to verify your identity and detect message tampering.
Authentication steps are so critical to keeping inboxes safe that many email clients won’t let you in without them. You can find out more about each one, plus other steps to make sure your messages reach the inbox in our Ultimate Guide to Email Deliverability. It’s free!
Here’s a list of the necessary protocols you should put in place if you want to avoid being a vehicle for spammers and scammers and getting included on an email blacklist.
Security step 1: Implement your Sender Policy Framework (SPF) authentication protocol. Your SPF protocol tells sending servers that a particular IP is authorized for use by your domain. If someone claiming to represent your domain uses an IP that’s not on this list, that signals to servers that they may be trying to sneak into town disguised as an associate of yours.
SPF protocols help in the fight against email spoofing attacks in which spammers try to use your good reputation to sneak past the internet’s sentries.
To activate this safety feature, you must add a text record to your domain settings (DNS records) with your domain host that lists your authorized IPs. This entry can also include instructions about how you want attempted hijackers to be handled.
A completed SPF record will look something like this if you must include individual IP addresses:
v=spf1 ip4:[list of your authorized IP 4 addresses] ip6: [list of your authorized IP 6 addresses] include:[other domain name] ~allSecurity step 2: Seal your email’s content with the DomainKeys Identified Mail (DKIM) protocol. This protocol attaches a cryptographic lock (a DKIM key) to your outgoing message header. No one can open locked messages unless they have a corresponding key and every open is recorded. Mailbox service providers can look at the DKIM record on an incoming email to determine if it has been opened during transit.
This protocol prevents internet outlaws from sneaking malicious content into your legitimate messages. Most ESPs add a DKIM signature to your sent emails before they leave the station.
Security step 3: Once you have your identity and content secured by the SPF and DKIM protocols, you let ISPs know by implementing Domain Message Authentication Reporting and Conformance (DMARC). This tool tells email receivers which protocols you are using and coordinates responses to hijack attempts with them.
A DMARC TXT record will look similar to this:
"v=DMARC1;p=reject;sp=quarantine;pct=100;rua=mailto:[Your Email Address];"Implementing this protocol enables you to keep an eye on potential security problems so you can stop them before they harm your subscribers or your reputation.
In addition to DMARC, you can also subscribe to third-party detection services such as Hotmark that will alert you to unauthorized activities related to your domains. As an added layer of protection for your subscribers, Hotmark also offers dedicated spamtraps (honeypots) to identify spammers who may have stolen your subscriber list.
Up next: Other methods you can use to determine if your IPs or domain are at risk or have been blacklisted.
Is my email on a blacklist? This is how you perform an email blacklist check

Blacklists don’t typically tell you if you land on them. You have to find out for yourself.
The first indicators that you’ve been blacklisted will typically show up in your email marketing platform analytics.
If your hard bounce rates are higher and your click rates lower than usual, that could indicate that you are being blocked by one or more email clients. Early warning signs that you may be headed for a block include increased spam complaints (above 0.2%) and reduced engagement.
Because each email client relies on its own internal records as well as public blacklists to decide how to treat your emails, one of your first stops when investigating changes to your performance should be those clients.
Look at your Google Postmaster Tools and Microsoft SNDS reports, email client feedback loops, and other ISP-generated data to find out how your reputation is faring.
Next, check your status on each of the major public blacklists. There are hundreds of published lists, but you don’t need to check every single one. Some blacklists are just not-so-thinly veiled extortion attempts that expect senders to pay to be removed.
Target your attention to blacklists, including the following, that ISPs consult and take seriously.
🤠Spamhaus
Spamhaus, or The Spamhaus Project, has a mission: To protect the world from spam. This multinational group of spam hunters oversees many, many blacklists held by ISPs and private enterprises alike.
Spamhaus takes their mission seriously. Their blacklists are dreaded by all internet outlaws.
ZEN, BCL, XBL, SBL, PBL, and DBL are the most well-known databases under Spamhaus’ jurisdiction. SBL is the one you’re most likely to encounter as an email marketer because of its habit of laying spamtraps. Buy lists and/or data and you’ll eventually run afoul of SBL.
🤠Spam and Open Relay Blocking System (SORBS)
Owned by Proofpoint, Inc., SORBs publishes a freely accessible DSN list (DSNBL) of more than 12 million host servers guilty of sending spam and malicious emails. The list includes active spammers and servers that have been hijacked or otherwise corrupted.
🤠SpamCop
SpamCop uses spamtraps and spam reports to compile their lists. Interestingly, they also use a point-based system to determine whether an address should be blacklisted. If you’ve made a slip-up but your subscribers are loyal and don’t mark you as spam, the benevolent SpamCop might let you go.
🤠Trend Micro Email Reputation Services Mail Abuse Prevention System (MAPS)
Trend Micro’s Email Reputation Services (previously known as the Mail Abuse Prevention System, or MAPS) enables you to look up an individual IP address reputation or access a global list of IPs that are considered safe. The website also tracks global spam volume by varying time intervals.
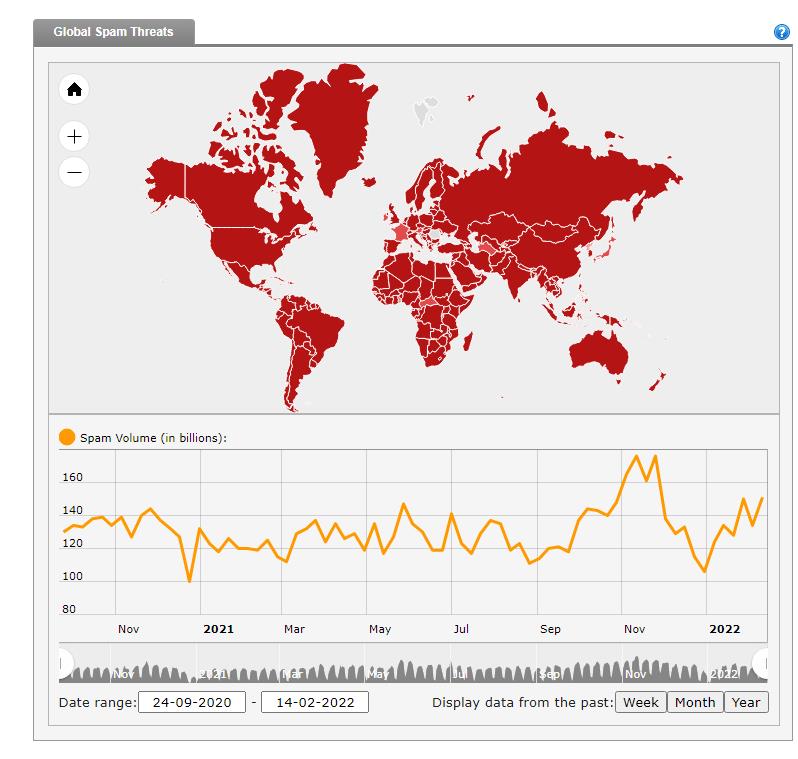
Spammers were very busy in Q4 of 2021.
🤠Invaluement
Invaluement primarily targets spambots, but that doesn’t mean that human email marketers should ignore it. If your domain or IP acts like a spambot, you’re at risk of catching Invaluement’s attention.
🤠Barracuda
Data company Barracuda keeps a comprehensive list of every address that tries to spam them or their clients. They’re a huge company, so the list is very well-stocked! If you spam data and/or security brands, chances are you’ll end up on Barracuda’s blacklist
🤠Open-Relays Verifying Engine Database List
Open-relay servers sometimes allow spammers to exploit configuration weaknesses and pass through their systems on the way to inboxes. The ORVEDB identifies open-relay machines or “junkmailers” that are accidentally or intentionally allowing spammers to leverage their systems.
Alternatives to checking every blacklist
Wow! Even if you just check the majors, that’s a lot of blacklists to monitor.
Blacklists are a big enough problem for bulk email senders that someone (more than one someone!) has created automated solutions to help you handle your reputation checks without spending all your time doing so.
Use multiple-list checking tools such as MxToolbox, Multirbl.Valli.org, GradeMyEmail, 250ok Blacklist Checker, or The Anti-Abuse Project to cut down on the time it takes to keep an eye on your domain and IPs.
If your domain or some of your IPs end up on one of these lists, it can wreak havoc on your deliverability and campaign performance. You gotta fix it! But how?
How to get your domain or IP delisted from an email blacklist

Welp, you’re there. Whether you made a few bad decisions or got caught up with the wrong crowd, you’re now on a blacklist. How does an email outlaw regain their good name?
It may not be as difficult as you think. Most internet folks are the forgiving kind. In fact, for some blacklists, all you have to do is wait. Behave yourself for long enough and they’ll forget all about you. Your IP will automatically drop off their list.
Email clients have (relatively) short memories too. If you implement the practices that you should be following to stay off blacklists, there’s a good chance you’ll eventually be allowed to reach their users’ inboxes.
To get your domain or IP removed from some blacklists, all you have to do is ask. Some blacklists have a self-service page where you can promise to do better and get your IPs delisted.
❕ If you’ve landed on a blacklist because of the actions of one of your server-mates on a shared IP, you’ll need to get your provider to do the asking.
Also, some blacklists offer expedited service in exchange for a fee. Be wary of these kinds of offers. Paying to be delisted can get expensive and may only be a short-term fix.
A blacklist may expect you to prove you’ve changed your ways before delisting your IPs or domain. The process for removal from these blacklists varies and most lists provide instructions and a contact link to get the process started.
For example, Spamhaus requires the owner of the IP to contact the Spamhaus blacklist (SBL) Team and demonstrate that the spam issue is fully resolved before it will delist an IP. If the SBL Team isn’t satisfied that there aren’t any ongoing issues, you’ll stay on the list.
Senders can fill out a form at BarracudaCentral to request removal from its list. SpamCop also provides a contact form for IPs that want to challenge their status.
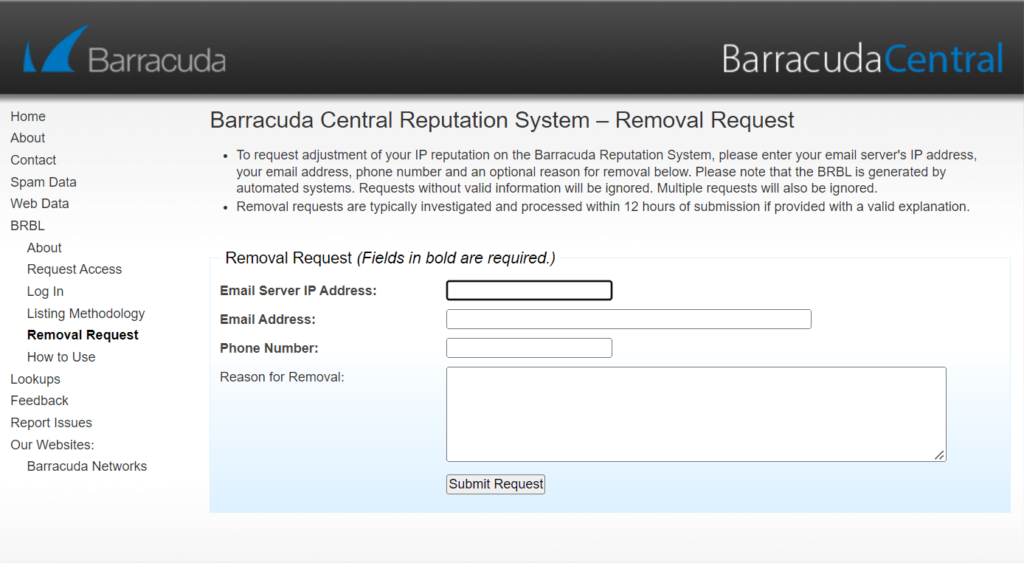
Be prepared to demonstrate that you’ve cleaned your subscriber lists and show proof of consent from subscribers who remain on the list. And, of course, demonstrate that you aren’t sending scammy emails.
Where should you begin your repair operations?
According to Oracle Marketing Cloud Consulting’s Director of Deliverability Strategy, B2C brands should start with Spamhaus. This digital bounty hunter sets the standard and being on its list can keep you out of 80% of your subscribers’ inboxes. B2B brands may feel a greater impact from being listed on SORBS.
Begin with the blacklists that have the greatest impact on your deliverability. There’s a good chance that fixing the cause of a listing with these lists will also fix the issue with others. Don’t forget to monitor your affiliates’ and partners’ compliance, too. Maintain your good behavior going forward and, hopefully, you won’t appear on any of these lists again.
Maintaining a good reputation is your best defense against deliverability problems and blacklisting. We take a deep dive into all the factors that can affect your domain reputation in our article covering How to Get a Great Domain Reputation. Why don’t you mosey on over and check it out, pardner?