Cyberattacks are rampant, and it’s only a matter of time until you’ll experience one. When that happens, your valuable email list is at risk, and so is your revenue and reputation as a sender. The best course of action is to be prepared and invest in services like Hotmark that can protect your email list and alert you in real-time of any dangers
Your email list database contains more than just emails and client details.
It contains every interaction you made with them, it’s the core of your business activity, it’s your reputation, and it’s incredibly vulnerable.
- 58% of small-to-medium businesses suffered from a cyberattack in 2018, and 85% will experience one in their lifetime.
- 27% of them have no cybersecurity protocols at all. A similar number of firms have difficulty implementing even the most rudimentary cyber defenses.
- In the first half of 2019, data breaches exposed 4.1 billion records.
Sobering statistics, forcing us to admit an uncomfortable truth about how real and dangerous data breaches are.
“88% of UK businesses have been breached in 2018!”
The above number was reported by VMWare’s Carbon Black, and the only reason we know this is probably due to the GDPR regulations, today the numbers are higher.
We encountered these stories far too often.
At Ongage, we talk to founders, email marketers, product people, and database managers all the time. We encountered these stories far too often.
That’s why we decided to do something about it, and thus Hotmark came to be!
Hotmark is a honeypot-as-a-service product that monitors your email database at all times, allows users to monitors their database, with 99.9% coverage and no human intervention.
Email lists are a source of revenue for many companies. Email marketing has an extremely high ROI, between $37 to $42 for every $1 you invest!
Once there’s a breach, that ROI drops, and the consequences are dire, an important point to remember when reading the chain of events below.
How Hotmark came to be
Hotmark was built to protect your email lists from both insider and outsider threats.
It’s the brainchild of Assaf Ben-Asher, Ongage’s CEO.
Assaf experienced first-hand how a data breach can affect someone’s life.
“Several years ago, one of my close friends suffered from a major breach. He discovered it only after experiencing a steep drop in client revenue.
At first, they couldn’t figure out what they were doing wrong, and only after a long while, they figured out that the problem didn’t stem from their campaigns, it was a breach, and at that point, it was too late.
The blow was devastating, and it resulted in lost revenue, time, morale, and reputation.”
Assaf couldn’t do much back then, and it broke his heart, seeing what it did to his friend and his business.
He decided to do something about it, “so no one would have to take such a hit.”

This is how Hotmark works
The spam traps you’re avoiding? They were planted by ISPs to smoke out the less legit email marketers.
Now they’re on your side!
Hotmark works similarly, it injects seed email addresses to your email list (these email addresses are also called honeypots), and from that point onwards, everything that happens to your email list is monitored.
Let’s see how it works.
What’s a breach point and how to define (and defend) it
A breach point is anything that `contains’ or `interacts’ with a database.

Typical breach points include:
- CRMs.
- Marketing automation platforms.
- Servers.
- Remote databases.
- Cloud access points.
- SVNs with access to your database access keys.
And it doesn’t end there. On top of the above-mentioned breach points, you have `human’ breach points like:
- First of all, you are a breach point!
- Employees.
- Business partners you change email lists with.
Yes, every employee or anyone with access to your database is a breach point!
How to set up a breach point in Hotmark
Your first task in Hotmark is to set a breach point, and it takes less than 30 seconds.
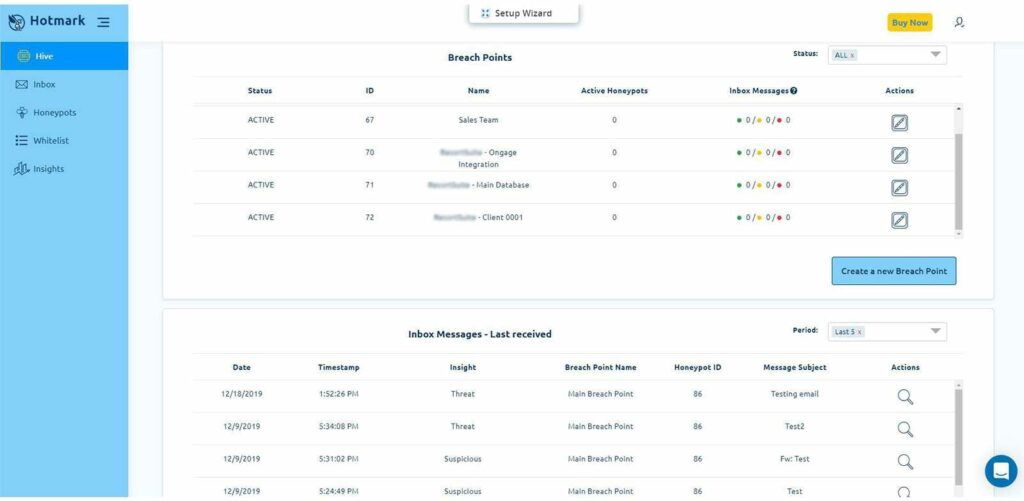
Once you defined a breach point, you can add honeypots to it, and they will monitor everything that happens there, alerting you the minute a threat is identified.
What are honeypots (and how they defend email databases)
Hotmark’s honeypots are email addresses (or mailboxes) that scan:
- The URLs inside any incoming email, including the redirection URLs, and report what is being sent through them.
- The content of the email analyzing all the moving parts, among others.
- And much more.
When you (or someone else) sends something, they identify it immediately because honeypots sit inside your email list and seem like ordinary emails.
Every campaign you’re sending, or that someone sends behind your back is monitored.

While you should hope it’ll report that everything is a-ok, there are other scenarios in which the honeypots will report that there’s something suspicious, or even a threat to your email list:
- Another domain (other than yours, or those you authorized) sent to this mailbox an email
- If one of the tracking parameters you sent is broken or was replaced, and someone else is collecting your hard-earned campaign revenue.
- One of the URLs in your emails is broken, resulting in an unapproved domain.
All scenarios should warrant your immediate attention because:
- The first two might mean you’ve been breached, and that your email list is out there for the highest bidder.
In the best-case scenario, they’re doing it secretly, collecting revenue behind your back. This will reduce your recipient’s loyalty, they will send them targeted offers that will try to capitalize on your business.
For example, imagine the following scenario:- You are a shoe brand, and your list got stolen.
- Your subscribers are used to seeing only emails from you about shoes.
- Suddenly they see emails from other shoe brands, and instead of 1 email per week, 10 shoe emails per week.
- The result is that your customer loyalty drops, and your bottom line gets a major hit.
- At worst, they might be hacking into your clients’ accounts. In addition, if you’re in the EU, you’ll have to deal with GDPR fines, and in the state of California, with CCPA. Breaches now have regulatory consequences, and if you were breached, you might find yourself fined for not taking measures against breach attempts.
- The latter is also important. Broken links can incur millions of lost revenue if left undetected. In reality, they cost companies who depend on email marketing just as much.

Honeypots help to identify and take care of the above scenarios; they are your secret security agents, helping you to monitor and respond, fast.
How to define a honeypot
After you create a breach point, press on the honeypots tab, and create your first honeypot.
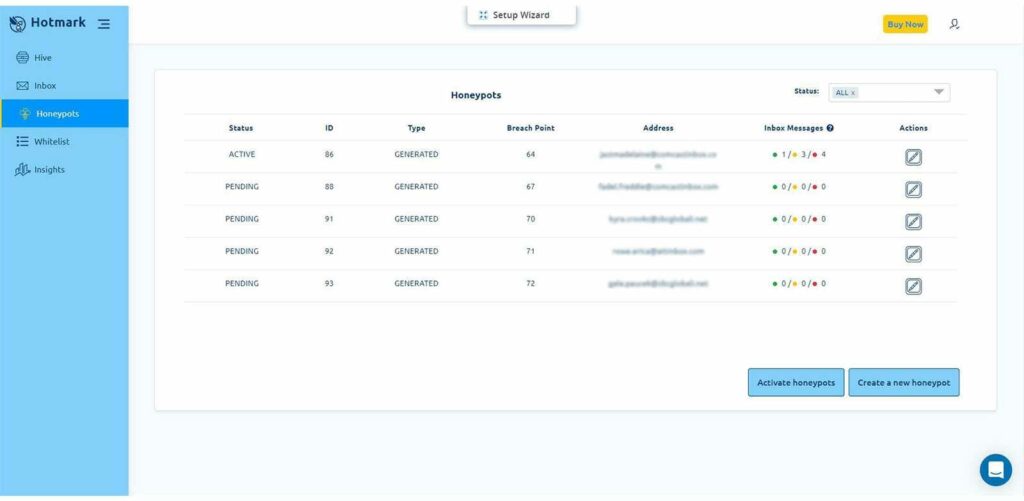
During the honeypot creation process, you’ll be able to associate it with a breach point.
Once you created the honeypot, you’ll have to activate it and plant it in your email list (your breach point).
- Go to your email inbox and activate the honeypot.
- Once it’s active, add it to your email list, it will not monitor activity otherwise.
Make sure that you associate the honeypot with only one breach point because when a breach attack happens, you have to pinpoint where the breach occurred, and fix it fast.
When you have the same honeypot on several breach points, you know that you’ve got breached, but not where the breach happened.
How many honeypots do I need?
It’s up to you to decide how many agents you have.
According to our experience, it’s recommended to have a 1 honeypot to 10,000 emails ratio.
When someone steals your email list, they can split it to cover their tracks. You need to have honeypots in every part of that list to track the breach on time.

Whitelisting your domains, the best way to identify threats
If you don’t want Hotmark to identify certain domains or URL parameters as threats, whitelist them (below).
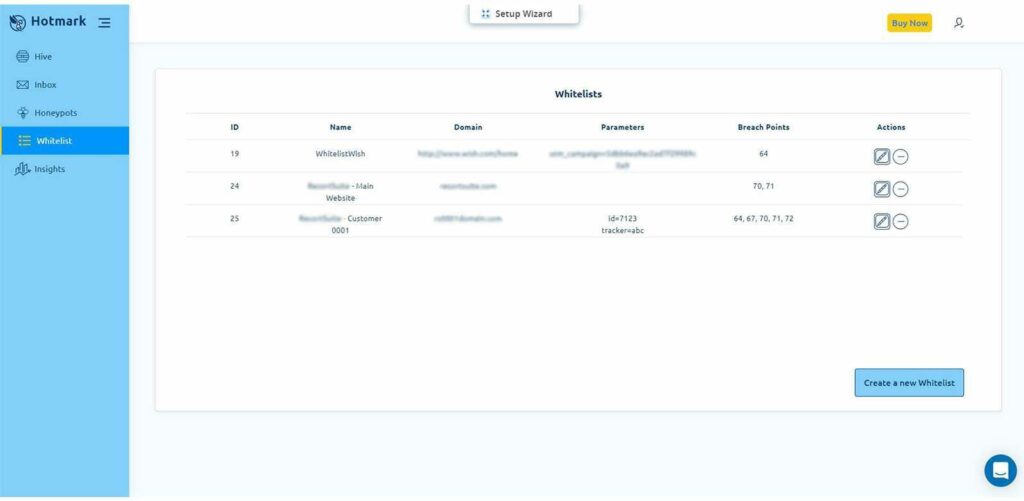
By whitelisting your domain, you’re telling Hotmark that a domain or a parameter is safe, which allows you to filter good results, saving you time and leading you to the threats you should pay attention to.
Notifications about whitelisted items will appear with a little green dot next to them.
Your Hotmark inbox
This is where you gain insights into the threats your email list is exposed to.
- If you have in your campaign a broken link or a parameter that was not whitelisted, you’ll get a suspicious notification (yellow).
- If you have a threat, i.e., an unidentified domain, you’ll get notified about a threat (red).
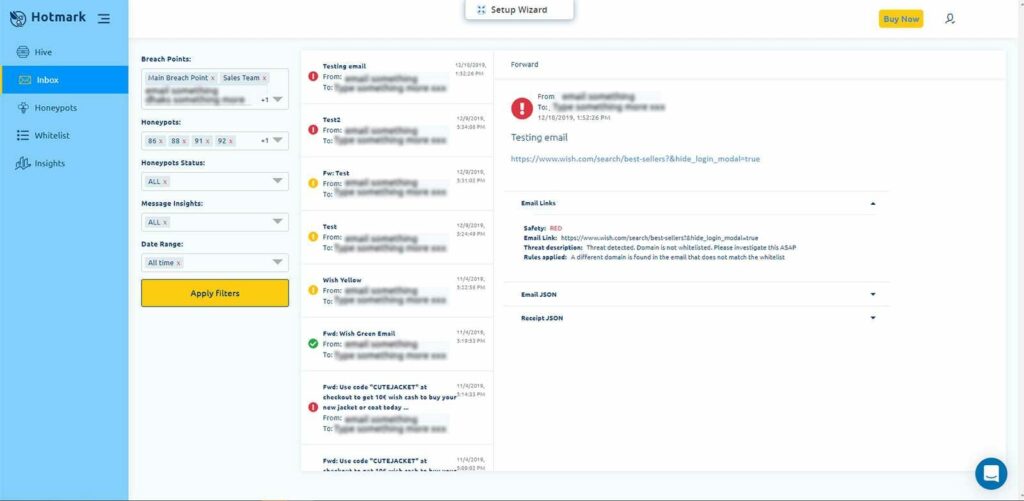
In your inbox, you’re able to filter incidents according to breach points, honeypots, and dates, allowing you to find what happened fast while providing information about the perpetrators.
Your insights and threat reports
In the Hotmark Insight tab, you’ll see full reports of the campaigns you sent.
If you have events that were classified as suspicious or as a threat, Hotmark will send you an incident report, allowing you to identify the threat, and providing you with all the information you’ll need to react to it fast.
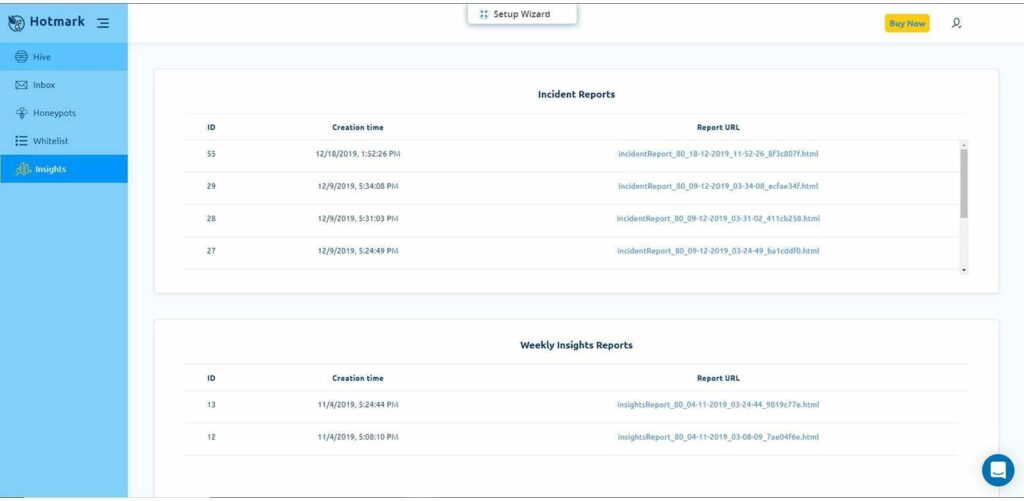
Here’s an example of an incident report:
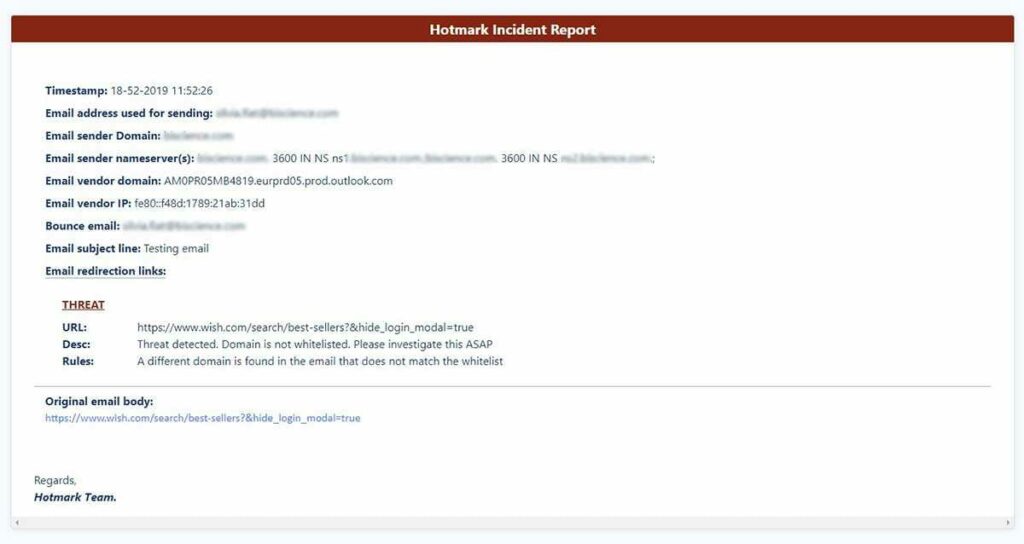
What to do after a threat has been detected?
In the case of an incident report, the first thing to do is to identify exactly what happened.
As noted, a yellow alert means the issue might be a broken link, which can be fixed quickly. If it’s a broken parameter, you might need to investigate it.
Campaign parameters, when changed, might be an indication that someone is abusing your email list.
In this case, consider halting your ongoing campaigns, and follow the “bread-crumbs” by checking the redirection links of the suspicious email, to find if it’s a false alarm or a threat.
If the incident report points to a data breach, then your first order of business is to contain it and report it to the law enforcement authorities.
Reporting is relatively easy, you pick up a phone and you talk. But containment? Not so much.
If you want to contain the breach fast, think preparation and response time, these are the most effective containment strategies according to the Ponemon report.
In the professional language, it’s called having a Cybersecurity Incident Response Plan (CSIRP).
A good one will:
- Identify the people authorized to make significant decisions.
- Define the roles and responsibilities of each respondent.
- Outline the communication flow and establish a work plan, with all the organizational functions which need to be included.
Once you have your CSIRP in place, and the authorities were notified, you’ll be able to use Hotmark to find where the breach came from.
It’s up to you to be pro-active, hunt down the perpetrators, confront them, and minimize the damage.
You can even tell them that they’ve been marked. Hotmarked! 😉
Offense is your best defense at this stage.
Do I need Hotmark?
While Hotmark won’t prevent an attack, it will allow you to quickly discover a data breach and respond to it with information that will help you to catch the responsible parties.

You can then act according to your CSIRP and:
- Contain the breach.
- Neutralize the threat.
- Assess the damage.
- Notify and report.
- Learn how and why it happened.
The more it takes for you to identify the breach, the more it will hurt your business.
In addition, your response time exposes you to additional fines from the regulators, Hotmark’s ability to help you respond fast is a lifesaver in breach events and daily operations.
Not sure? Sign up for a free trial
You don’t need any IT help, or coding skills to run Hotmark. A quick set up wizard will take you through all the required steps, making sure at the end that the honeypots are actively monitoring your database against threats.
On top of that, once it’s set, your job is done. There’s no need for any further fiddling, Hotmark will update you when something happens.
Sign up now for a free trial and protect your email list, your revenue, your employees, and your organization.